In today’s digital landscape, cyber threats are an ever-present danger for businesses, organizations, and individuals. With the growing sophistication of cyberattacks, having a well-structured incident response (IR) plan is crucial to mitigating potential damage and ensuring business continuity. This blog explores the key components of incident response, its importance, and best practices for an effective response strategy.
What is Incident Response?
Incident response refers to the systematic approach an organization takes to detect, analyze, and respond to security incidents. These incidents may include data breaches, ransomware attacks, phishing attempts, malware infections, and other cyber threats. A well-defined IR strategy helps minimize the impact of security incidents and prevents future occurrences.
Why is Incident Response Important?
Minimizes Downtime: A rapid response can limit the disruption caused by security incidents, ensuring that operations resume quickly.
Protects Sensitive Data: Proper handling of security incidents prevents data theft, ensuring compliance with privacy laws and industry regulations.
Reduces Financial Loss: Cyber incidents can lead to significant financial repercussions. A solid IR plan can help reduce costs associated with data recovery, legal fees, and reputational damage.
Maintains Customer Trust: Promptly and transparently addressing incidents reassures customers that their data is protected, preserving the organization’s credibility.
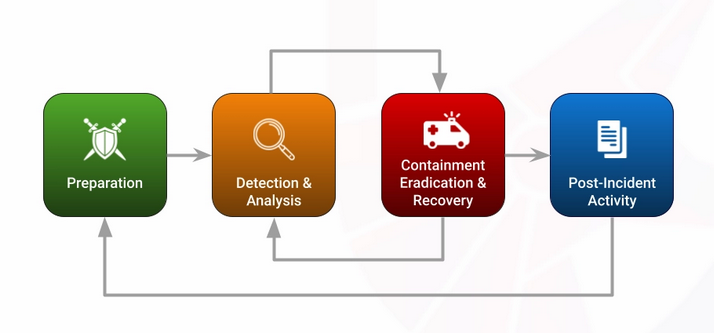
The Incident Response Lifecycle
The National Institute of Standards and Technology (NIST) outlines a well-structured IR lifecycle that consists of four main phases:
1. Preparation
Develop an IR plan and establish response teams.
Conduct risk assessments and identify critical assets.
Implement security tools such as firewalls, intrusion detection systems (IDS), and endpoint protection.
Regularly train employees on cybersecurity best practices and phishing awareness.
2. Detection and Analysis
Continuously monitor network traffic for suspicious activities.
Use security information and event management (SIEM) tools to detect anomalies.
Gather and analyze logs to determine the nature and scope of an incident.
Categorize and prioritize incidents based on severity.
3. Containment, Eradication, and Recovery
Isolate affected systems to prevent further spread of the attack.
Identify and eliminate the root cause of the incident.
Restore systems from secure backups to ensure data integrity.
Apply security patches and reinforce defenses to prevent recurrence.
4. Post-Incident Review
Conduct a thorough analysis to assess the response effectiveness.
Document lessons learned and update the IR plan accordingly.
Strengthen security measures based on insights gained from the incident.
Communicate findings with stakeholders and ensure regulatory compliance.
Best Practices for an Effective Incident Response Strategy
Develop a Clear Incident Response Policy: Define roles, responsibilities, and procedures for handling security incidents.
Utilize Threat Intelligence: Leverage real-time threat intelligence to proactively detect and respond to cyber threats.
Automate Incident Detection and Response: Deploy AI-driven security solutions to detect threats faster and improve response times.
Regularly Test the IR Plan: Conduct simulated attacks (red team exercises) to evaluate response effectiveness.
Establish Communication Protocols: Define internal and external communication strategies to handle incidents efficiently.
Collaborate with Law Enforcement and Industry Experts: Work with cybersecurity professionals and legal teams to ensure a compliant and effective response.
Conclusion
Incident response is an essential aspect of any cybersecurity strategy. By adopting a proactive approach and implementing a well-structured IR plan, organizations can effectively mitigate risks, protect sensitive data, and maintain business continuity. As cyber threats continue to evolve, staying prepared and continuously improving response capabilities will be key to safeguarding digital assets in the future.
Phelix Oluoch
Founder, PhelixCyber
W: PhelixCyber.com